Identity
Identity is an essential factor in our lives. We live in a society where everything we do revolves around identity. And with easy access to it, our industrial aspects can truly shine. In reality, our identities are slowly leaving the paper-based old system and moving towards digital identity.
As the importance of owing self sovereign identity, blockchain and digital identity could really become a great combination. With new innovations coming in many fields, the identity sectors still lack digitization. And so, blockchain can surely help tackle all issues and gift us a decentralized identity solution.

What is Identity Management ?
Identity management (ID management) is basically the organizational process for identifying, authenticating and authorizing individuals or groups of people to have access to applications, systems or networks by associating user rights and restrictions with established identities.
Identity Access Management is to “grant access to the right users in the right context, from a user’s system on boarding to permission authorizations to the off boarding of that user as needed in a timely fashion.”
In the same way, you can manage and control the access to be allowed to your Identity (IDENTITY ACCESS MANAGEMENT) stored in DigiID.
WHY IDENTITY ACCESS MANAGEMENT IS REQUIRED ?
Identity theft is now so common that consumers barely have time to react to one breach before another is announced. According to the 2019 Identity Fraud Study from Javelin Strategy & Research, the number of consumers who were victims of identity fraud fell to 14.4 million in 2018, down from a record high of 16.7 million in 2017. However, identity fraud victims in 2018 bore a heavier financial burden: 3.3 million people were responsible for some of the liability of the fraud committed against them, nearly three times as many as in 2016. In 2018, 15 percent of all complaints were related to identity theft. Identity theft claims fell from 2015 to 2018 by 9.3 percent, but began to increase again in 2018 and were up 19.8 percent from 2017 to 2018.


Further, it will eliminate the possibility that person’s personally identifiable information (PII2) will be monetized and sold by corporate data giants for commercial gain.
This shows how the Identity Theft is the main area for Cyber Crimes. It’s high time to change the way we manage our Identity either physically or digitally. It’s time to give thought whether are our Digitally stored identities really safe ??
"Grant Access To The Right Users In The Right Context, From A User’s System Onboarding To Permission Authorizations To The Off boarding Of That User As Needed In A Timely Fashion"
Digital Identity Management Systems at Present!
Every kind of business depends on the evolving technologies that tend to take advantages of new opportunities. However, with every new tech comes a whole different set of challenges. In reality, the identity management system needs to have the speed to ensure every user gets their query solved in time.
More so, it also needs to have a higher security level. However, the IT managers struggle hard to maintain both simultaneously. Moreover, attacks and faulty applications increase the difficulty of managing digital identity as well.
Thus, the importance of digital identity is more than ever. Anyhow, due to the lack of proper security issues, the scenario at present isn’t the best. So, many users face identity issues that cause a massive problem in their social life as well. To ensure a proper management system, all the problems need to be solved fast.
Why Is Digital Identity Impotent?
1. The importance of digital identity is prominent than ever for some major reasons. These are Without a proper ID, getting access to education, banking, or health is difficult for people, and this includes refugees as well.
2. Getting rid of a paper trail is more important as that system doesn’t offer people the best results due to the lack of speed and corruption.
3. There’s no global cooperation with IDs, so, digital identity can enable that as it’s a digital-based identification. As you can see, the importance of digital identity is absolutely massive.
Moreover, we use digital identity everywhere now. It not only makes our life simpler, but it also increases efficiency. Moreover, in every app, device, or service, we have separate identification. And so, the importance of digital identity in those services is huge. On the other hand, the importance of digital identity in the Enterprise sector is also prominent. In reality, the enterprise companies need to have a full clarification of every single employee. It becomes a necessity to ensure efficiency in this sector, and thus, the use of digital identity technologies is increasing as well.
The Self-Sovereign Identity (SSI)
“Self-Sovereign Identity is the next step beyond user – centric identity, and that means it begins at the same place: the user must be central to the administration of identity.”
By Cristopher Allen, blockchain and cryptography pioneer, co-author of the TLSSecurity Standard
Self-sovereign Identity is an identity that is owned and controlled by its owner without the need to rely on any external administrative authority and without the possibility that this identity can be taken away. It can be enabled by a decentralized identity eco-system that facilitates the recording and exchange of identity attributes, and the propagation of trust among participating entities.
Self-sovereign identity (SSI) is a term used to describe the digital movement that recognizes an individual should own and control their identity without the intervening administrative authorities. SSI allows people to interact in the digital world with the same freedom and capacity for trust as they do in the offline world.
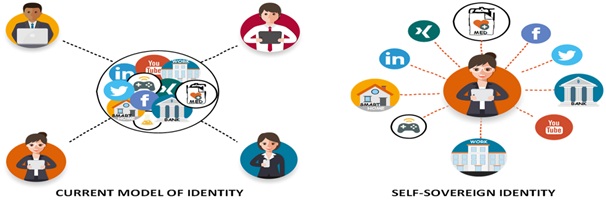
Self-sovereign identity (SSI) brings the same freedoms and personal autonomy to the internet in a safe and trustworthy system of identity management.
SSI means the individual (or organization) manages the elements that make up their identity and controls access to those credentials– digitally. With SSI, the power to control personal data resides with the individual, and not an administrative third party granting or tracking access to these credentials.
The SSI identity system gives you the ability to use your digital wallet and authenticate your own identity using the credentials you have been issued. You no longer have to give up control of personal information to dozens of databases each time you want to access new goods and services, with the risk of your identity being stolen by hackers.
This is called “self-sovereign” identity because each person is now in control of their own identity—they are their own sovereign nation. People can control their own information and relationships. A person’s digital existence is now independent of any organization: no-one can take their identity away.
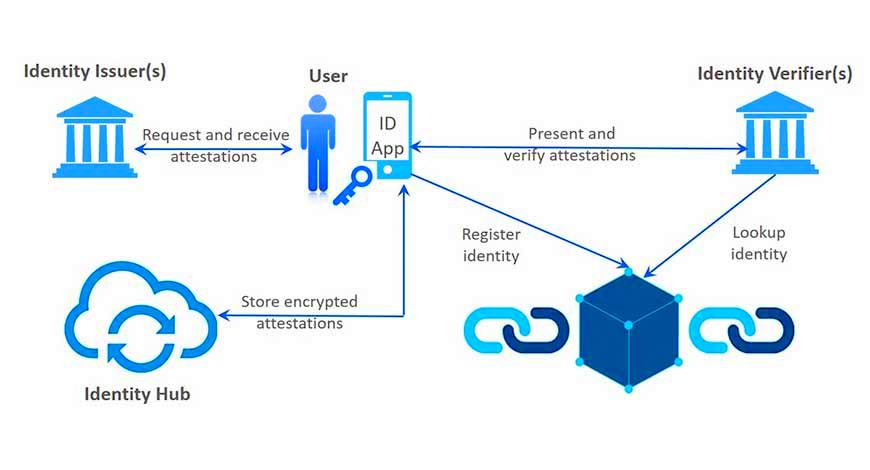
Digital Identity Blockchain: How Can Blockchain Help?
Blockchain can be a great solution for decentralized identity. In reality, blockchain for enterprise can easily power the framework of the decentralized identity. Not only does it offer a readymade infrastructure, but it also offers security for it. So, if the enterprise starts to use it, it will definitely solve the issue that comes with third party companies misusing information.
Creating DIDs
I think you already know that blockchain addresses are extremely unique. And you can use these addresses for making DIDs. Moreover, these are all cryptographically secured, and the owner generates it themselves.Blockchain can be a great solution for decentralized identity. In reality, blockchain for enterprise can easily power the framework of the decentralized identity. Not only does it offer a readymade infrastructure, but it also offers security for it. So, if the enterprise starts to use it, it will definitely solve the issue that comes with third party companies misusing information.


Creating DIDs
I think you already know that blockchain addresses are extremely unique. And you can use these addresses for making DIDs. Moreover, these are all cryptographically secured, and the owner generates it themselves.
Registry for All DIDs
Another great digital identity blockchain platform usefulness would be using it as a DID registry. Basically, you can store all the information of the IDs to the immutable ledger storage. This way, no one can access your ID anytime and even steal the information.
Credential Notarization
It’s similar to putting seals on your ID. Here, the platform can offer to put a hash address to that information on the digital identity blockchain platform. However, it doesn’t mean it will only store the credentials on the ledger.
It would mean that it would act as a timestamp and moreover, offer an electronic seal. For example, let’s say a university would provide the hash for a diploma on the platform after the student graduates. It will help the student to know when the diploma was issued along with proof of his certificates. Thus, when he uses the certificate for a job or other purpose, he can show that this is the certificate that had the hash function from the university.
In reality, it can be a great way to change how people handle the certification from any respected university. Moreover, it gets rid of the falsifying certificate issues that many companies face while hiring a new employee.


Consent and Access Rights
You can also use the digital identity blockchain platform to control who can access your credentials and who can’t. For example, you might want to share some of your information on various platforms but maybe for a certain amount of time.
You could also give access to companies that you want to work with to check if you have the notarized credentials or not. Anyhow, you can do that in the form of transaction with an expiration date. So, when it expires, it would be back to the way it was. On the other hand, the company that you grant access would then have to delete the information and prove it on the platform that they did so.
Using Smart Contract Features
There’s plenty of use of smart contracts. Moreover, you’ll need your identity every time for official contracts of any sorts. For example, in insurance, healthcare, or any form of services. So, you can use your identity as a proof in smart contracts triggering a payment system along the way.
SYSTEM BASED ON ZERO KNOWLEDGE PROOF
Zero Knowledge Proof is the method where one party (Prover) can prove that a specific statement is true to the other party (Verifier) without disclosing any additional information. The essence of a zero-knowledge proof is that it is trivial to prove that someone possesses knowledge of certain information by simply revealing it. The challenge is to justify such possession without revealing the information itself or any additional information.
Zero-Knowledge Proof creates trustless transactions that protect users’ privacy using mathematics. As such, Zero Knowledge Proof improves verification processes to such an extent that one party can prove to another party that a given statement is true, without revealing any information about that statement.

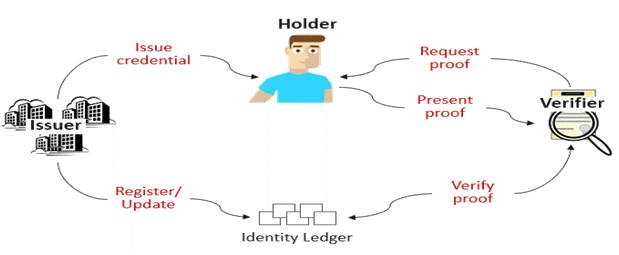
THE 3 PILARS IN IDENTITY MANAGEMENT WITH BLOCKCHAIN
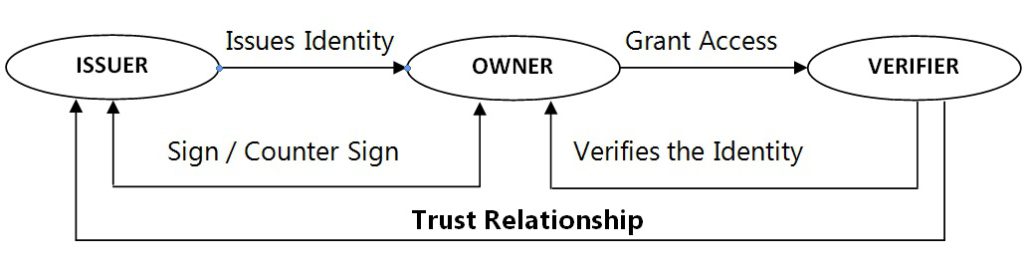
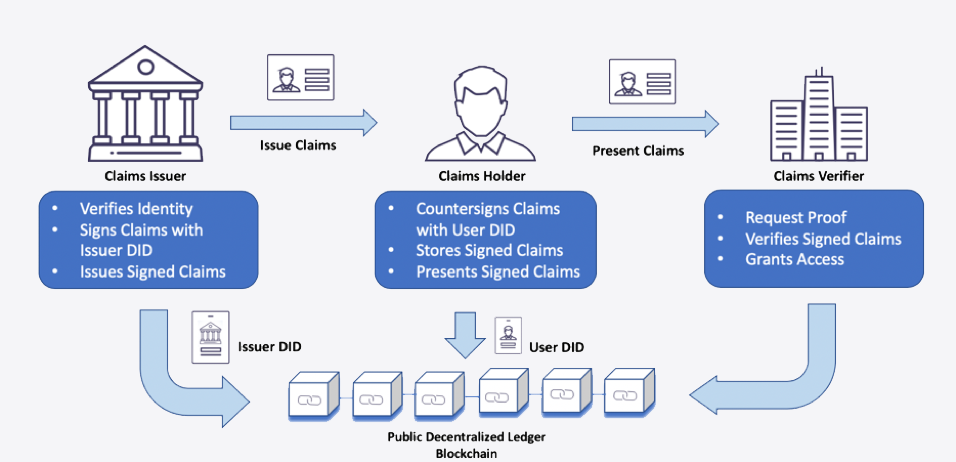
OWNERS, ISSUERS AND VERIFIERS
When talking about leveraging blockchain technology for identity management, it’s important to note that there are three different actors in play: identity owners, identity issuers and identity verifiers.
The identity issuer, a trusted party such as local government, can issue personal credentials for an identity owner (the user). By issuing a credential, the identity issuer attests to the validity of the personal data in that credential (e.g. last name and date of birth). The identity owner can store those credentials in their personal identity wallet and use them later to prove statements about his or her identity to a third party (the verifier).
A Credential is a set of multiple identity attributes and an identity attribute is a piece of information about an identity (a name, an age, a date of birth).
Credentials are issued by second parties whom attest to the validity of the data inside the credential. The usefulness and reliability of a credential fully depends on the reputation/trustworthiness of the issuer.